Background
In previous articles, we have learned about the bitcoin blockchain, the flagship of cryptocurrency. Subsequently, we learned about Ethereum that features smart contracts on top of its cryptocurrency Ether. Smart contracts allow developers to create decentralized applications (
Both bitcoin and Ethereum are amazing blockchain platforms. However, both are facing some very challenging issues, one of them is scalability. According to Wikipedia, the transaction processing capacity of the bitcoin network is limited by the average block creation time of 10 minutes and the block size limit. The transaction rate for bitcoin is between 3.3 and 7 transactions per second.
Ethereum does not fare better, its transaction rate is 15 transactions per second. Comparatively, VISA’s transaction rate is 45,000 transactions per second. Therefore, both platforms fall short in developing practical enterprise applications at the moment.
To overcome the limitations of the blockchain technologies for enterprise usage, Hyperledger was created with the vision to provide viable blockchain solutions for industries and businesses. Hyperledger is an open source effort created to advance cross-industry blockchain technologies hosted by The Linux Foundation.
The Mission of Hyperledger
The philosophy of Hyperledger is
“Only an Open Source, collaborative software development approach can ensure the transparency, longevity, interoperability, and support required to bring blockchain technologies forward to mainstream commercial adoption.” –
Indeed, the Hyperledger project has been a collaboration of players from various industries and organizations in technology, finance, banking, supply chain management, manufacturing, IoT and more. Since its inception in December 2015, it has managed to enlist many prominent members that
The mission of Hyperledger comprises some ambitious goals, as illustrated in the following figure,

The Hyperledger Greenhouse
Hyperledger itself is not a platform, but it is an umbrella body that incubates and promotes a range of business blockchain technologies. The technologies include distributed ledger frameworks, smart contract engines, client libraries, graphical interfaces, utility libraries, and sample applications. The umbrella strategy was able to accelerate innovation of DLT components by encouraging the re-use of common building blocks and components(hyperledger.org, 2018).
The Hyperlegder projects known as The Hyperledger Greenhouse consists of five projects and five tools, as shown in the figure below:
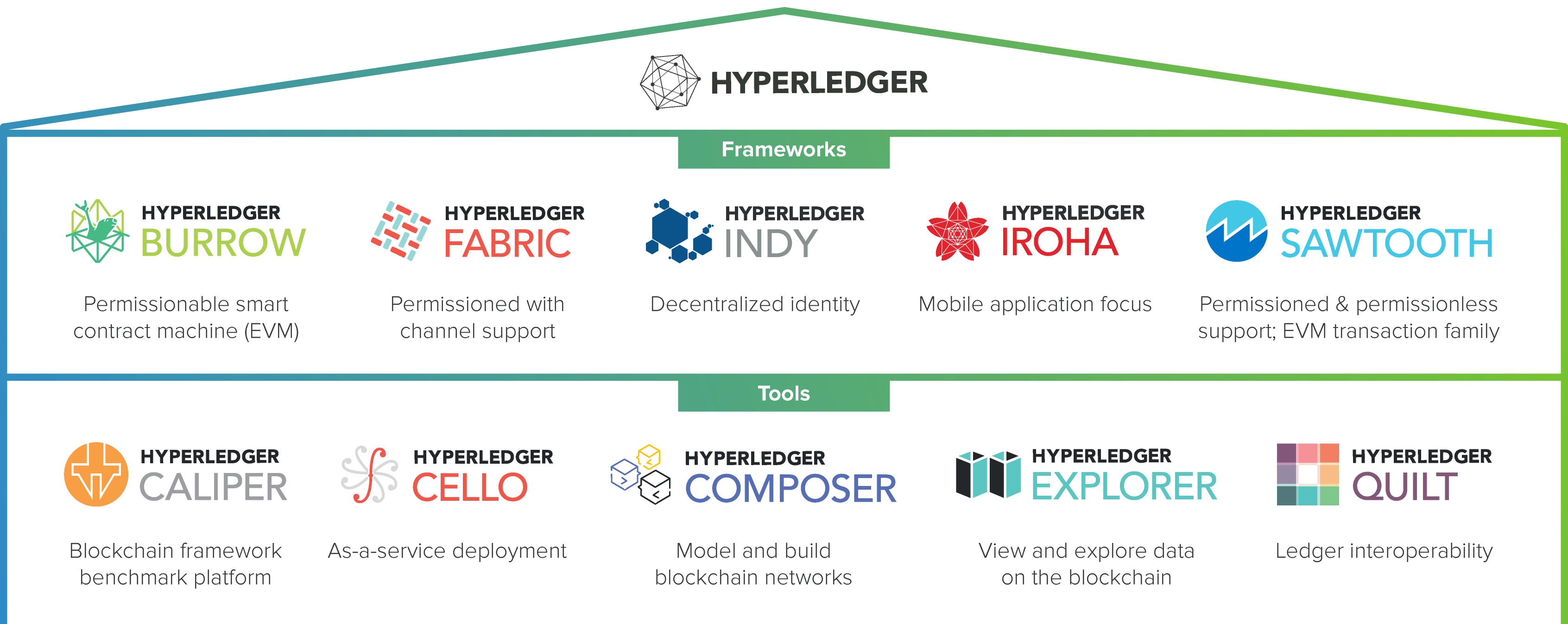
Each of the frameworks operates differently but they also allow certain interoperability among themselves. Hyperledger frameworks are generally permissioned (private)blockchains. It means that the parties need authentication and authorization to participate on the blockchain networks.
I will try to explain some of the frameworks and tools in simple language in a series of future articles. I am not an expert on Hyperledger but I have a decent understanding of the technologies via theories and practice. Recently I have enrolled in a Hyperledger course hosted by the Linux Foundation and managed to obtain a certificate of achievement. I am willing to share my knowledge with you.

Open Source and Open Governance
The success of Hyperledger is based on the concepts of open source and open governance. The concept of open source means that an open source software is a software that is made freely available and may be redistributed and modified. In other words, anyone has the ability to view the code, use the code, copy the code, modify the code, and, depending on the open source license, contribute back changes. (hyperledger.org, 2018)
On the other hand, open governance means that technical decisions for an open source project are made by a group of community-elected developers voted in from a pool of active participants. These decisions include things such as which features to add, how, and when to add them. (hyperledger.org, 2018). Hyperledger has formed a Technical Steering Committee(TSC) to implement open governance pertaining to the Hyperledger projects. You can read about Hyperledger’s open governance by following this link
https://www.hyperledger.org/blog/2017/09/06/abcs-of-open-governance
That’s all for now. I will discuss why Hyperledger blockchain frameworks are better designed for enterprises than the public permissionless blockchains in coming articles.
Meanwhile, you may want to register for the Hyperledger Global Forum in