The meetup was at HelloGold office , KL on Friday 23, Nov.
Speakers:
- Petar Tsankov-Chief Scientist/co-founder of ChainSecurity AG & Senior Researcher at the ICE center. ETH Zurich.
- Andras Kristof- Founder and Advisor of Akomba Labs
- Lai Ying Tong- Researcher at Ethereum Foundation
- Ken Chan
The session began with Ken Chan introducing the audience about Zero-Knowledge Proofs. I was sure many developers among the audience understand what it is but the concept sounds strange to me. Fortunately, Ken was good in demonstrating the concept by using the scenario of the American presidential election involving Trump and Clinton as well as a “live demo” with Harith of HelloGold as the co-actor.
Apparently, the Zero-knowledge proof method, or more exactly zk_SNARKS, is a consensus protocol used by Zcash to validate its shielded transactions that are fully encrypted on its blockchain. According to Zcash(https://z.cash/technology/zksnarks/), the acronym
Zcash further pointed out that “Zero-knowledge” proofs allow one party (the prover) to prove to another (the verifier) that a statement is true, without revealing any information beyond the validity of the statement itself. For example, given the hash of a random number, the prover could convince the verifier that there indeed exists a number with this hash value, without revealing what it is.
Ken illustrated the process of Succinct and Non-interactive using a diagram, where the prover begins by generating a proof string and then the verifier needs to verify the proof string, as shown below:

The above process is actually more complex than illustrated in the diagram. According to Zcash,
Computation → Arithmetic Circuit → R1CS → QAP → zk-SNARK
Here is an example of what an arithmetic circuit looks like for computing the expression (a+b)*(b*c) :

The output is then verified by the verifier. However, Ken pointed out that the process might be compromised by some malicious codes which he called toxic waste that produce false proofs. Ken concluded with the following points:
Why ZK SNARKs?
- Strong cryptography research by Zcash team
- Math-based- not coin joining
- Short proofs
Why not ZK SNARKS?
- Trusted setup for every contract
- No transparency for counterfeiting
- Computationally expensive
Next, Dr.Petar from ChainSecurity discussed the importance of
According to Dr.Petar, more USD$1 billion have been stolen this year due to crypto hacks. He stressed that writing secure smart contracts is difficult. Developers might fail to see bugs and security flaws, therefore we need to audit the smart contracts. However, currently, most audits are done manually and tend to miss many issues. Furthermore, in the post-development stage, most anomalies are invisible.
To work around the aforementioned issues,
More information on security audit can be found on ChainSecurity website.
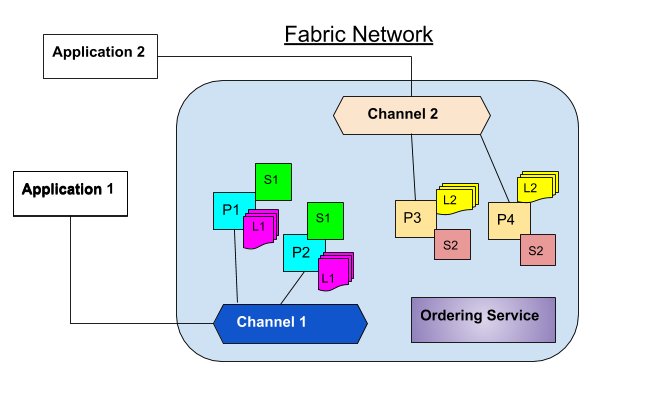
The final topic was scaling presented by Andras Kristof and Lai Ying Tong. This is a topic where all Ethereum enthusiasts are concerned about. According to the speakers, the solution is to develop a two-layer architecture. Layer 1 is called serenity which comprises sharding,
In more details, the layer 1(serenity) structure includes the Main Chain(provides staking and PoW), the Beacon Chain((provides random number and PoS), the Shard Chain(provides data) and VM(provides state execution result).
For the payment channels, there are two channels, the Open Channel and the Close Channel. The transactions include blockchain transactions and Off-chain payments. Besides that, Lai also spoke on payment channels on the lightning network. The layer2 solutions are to move state-modifying operations off-chain, which include payment channels and state channels.
Besides that, Lai also covered topics on sidechains, plasma